Github action defined as submodule in a repo #26426
-
|
If action defined over a subdir you can refer to it like:
But this fails if I get following error like So I think when action is defined in a public repo, git-runner clones it, but doesn’t clone the sub-modules defined in them. Hence I am getting above error. Workaround is to check-in the whole action code in the path, but it’s not a best way when you have advantages of adding it as sub-module thingy. |
Beta Was this translation helpful? Give feedback.
Replies: 13 comments
-
|
Couldn’t you refer directly to the submodule repo (or a directory in it) with the The only disadvantage I see is that if the submodule HEAD has to exactly match the action ref you’ll have to update both at the same time. |
Beta Was this translation helpful? Give feedback.
-
|
Thanks @airtower-luna. More Info: To be frank, we can bypass this check by committing whole action code/repo as part of our application repo, but thought sub-module approach would be neater. PS: I understand that, it is not good to by pass this check in any way unless we get approval from admins 😊 😉 |
Beta Was this translation helpful? Give feedback.
-
|
You need to checkout with submodules: See https://github.com/actions/checkout:
|
Beta Was this translation helpful? Give feedback.
-
|
Yes @Simran-B. But Let me know if this clarifies. Thanks |
Beta Was this translation helpful? Give feedback.
-
|
I guess in that case you’ll unfortunately have to clone the repository manually, using git commands in a That said, it seems a questionable choice to use Github for hosting and CI and then not allow the official actions… Maybe you can convince your admins to allow these basic actions, or at least create forks within your organization? |
Beta Was this translation helpful? Give feedback.
-
|
We think it would be a good idea when the checkout action supports clonimng private submouldes by providing a different SSH key. The PAT token is not owrking in many cases since it is bounded to a specific user. With a SSH key pair you can clone the repo as submodule by setting up a deploy key. actions/checkout#287 |
Beta Was this translation helpful? Give feedback.
-
|
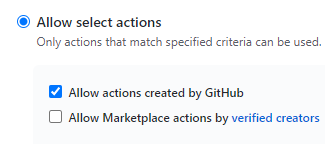
Sorry, I misunderstood the problem. The easiest solution would indeed be to allow Actions by GitHub: (I wonder if local actions need to be added to the allowlist if Allow select actions is enabled…)
PuneethaPai:
Actually no. It’s a chicken and egg problem. The runner starts out with a fresh virtual environment. You want to checkout the repo using a local copy of the checkout action, but it doesn’t exist - you first need to checkout the repo… The runner seems to retrieve public actions automatically, so that the workflow run can be bootstrapped by fetching |
Beta Was this translation helpful? Give feedback.
-
|
Weird, if I fetch the three core files of the checkout action with curl, I can use it as local action to checkout a repo. However, the following errors occur when Error: Unable to process command ‘::add-matcher::/home/runner/work/olive-ci/olive-ci/temp/checkout/dist/problem-matcher.json’ successfully.
With
BTW. local actions do not need to be added to the allowlist. And it’s not limited to the very repo, it can be any repo in the same account / organization. |
Beta Was this translation helpful? Give feedback.
-
|
I was thinking, github runners clone actions repo before running them.
Can’t they clone submodules in the repo as well? Is that a bad feature request? Thanks |
Beta Was this translation helpful? Give feedback.
-
|
Huh. Local action means an action whose repository is in the same user account or org. It’s not restricted to the very repository. That means, you can simply fork |
Beta Was this translation helpful? Give feedback.
-
|
As I said above we are dependent on our admins for this too.
|
Beta Was this translation helpful? Give feedback.
-
|
Ah, I didn’t read that as forking. Well, if they don’t give you enough permissions, how are you supposed to do your job? If they don’t trust you as employee, then they shouldn’t trust GitHub or other cloud services either and go for something on-premise. |
Beta Was this translation helpful? Give feedback.
-
|
Thanks everyone. I’ll share this thread with admins and hopefully I’ll be able to pursued them to realise the silliness of disabling public action and remove this blocker. Thanks |
Beta Was this translation helpful? Give feedback.

I guess in that case you’ll unfortunately have to clone the repository manually, using git commands in a
runstep.That said, it seems a questionable choice to use Github for hosting and CI and then not allow the official actions… Maybe you can convince your admins to allow these basic actions, or at least create forks within your organization?